AWS Security Groups
AWS Security Groups are virtual firewalls that control inbound and outbound traffic to AWS resources, such as EC2 instances. They provide a way to manage access to resources by defining rules that allow or deny traffic based on criteria such as IP address, protocol, and port number.
Key Features
- Stateful Filtering: Security Groups are stateful, meaning that if you allow an inbound request from a specific IP, the response is automatically allowed, regardless of outbound rules.
- Rules-Based Control: Define rules to allow or deny traffic based on source IP, destination IP, port, and protocol. Each Security Group can have multiple inbound and outbound rules.
- Apply to Multiple Resources: Security Groups can be applied to multiple EC2 instances, ensuring consistent security configurations across your infrastructure.
- Default Security Group: Each VPC comes with a default Security Group that allows all inbound and outbound traffic unless modified.
- Dynamic Updates: Changes to Security Group rules are automatically applied to all associated resources, providing flexibility in managing access control.
Common Use Cases
- Application Segmentation: Use Security Groups to segment applications into different tiers (e.g., web servers, application servers, database servers) and control traffic flow between them.
- Restricted Access: Restrict access to specific resources, such as databases, by allowing only traffic from trusted IP addresses or other Security Groups.
- Compliance and Security: Implement security controls to meet compliance requirements by defining precise access rules for sensitive resources.
- Testing and Development: Use Security Groups to create isolated environments for testing and development, ensuring that only authorized traffic can access your instances.
Architecture Overview
The following diagram illustrates how AWS Security Groups operate within a VPC:
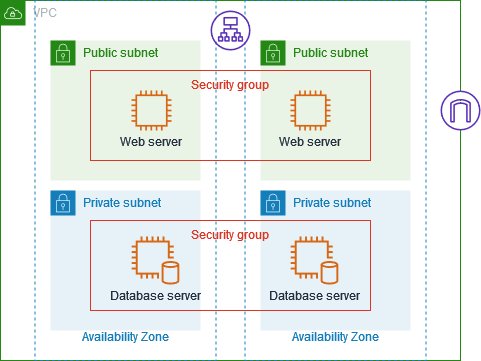
- Security Group Rules: Define inbound and outbound rules that control traffic to and from instances.
- Instance Association: Attach Security Groups to instances to enforce the defined rules.
- Traffic Filtering: Security Groups filter traffic based on the rules applied, allowing or denying traffic as specified.
- Dynamic Updates: Changes to Security Group rules are automatically reflected in associated instances.
Integration with Other AWS Services
AWS Security Groups integrate with various AWS services to provide comprehensive security controls:
- AWS EC2: Control traffic to and from EC2 instances using Security Groups.
- AWS Elastic Load Balancer (ELB): Apply Security Groups to ELB to manage access to your load balancers and backend instances.
- AWS RDS: Use Security Groups to control access to RDS instances, ensuring only authorized traffic can reach your databases.
- AWS Lambda: Apply Security Groups to Lambda functions within a VPC to manage access to resources.
- AWS Elastic Beanstalk: Configure Security Groups for Elastic Beanstalk environments to manage access to your application instances.
Things to Remember for the Exam
- Stateful vs. Stateless: Understand the difference between stateful Security Groups and stateless Network ACLs. Security Groups are stateful, meaning responses to allowed inbound traffic are automatically allowed.
- Rule Management: Know how to configure inbound and outbound rules, and how to manage multiple rules within a Security Group.
- Default Security Group: Be familiar with the default Security Group settings and how they apply to instances in a new VPC.
- Resource Association: Understand how to associate Security Groups with different AWS resources, including EC2 instances, ELB, RDS, and Lambda functions.
- Traffic Flow Control: Review how Security Groups manage traffic flow between different tiers of an application and across multiple resources.
- Security Group Limits: Be aware of the default limits for Security Groups, including the maximum number of rules and Security Groups per instance.